How do you create a strong password? Easy: You mash your keyboard for a few seconds until you have a 50-character hunk of gibberish, then you copy and paste that into a password manager so you don’t have to actually remember what it is.
Photo: Pixabay
There are other tricks for creating strong passwords, but there are only two rules you really have to remember: make it long and make it difficult to guess (or brute-force). “mycatiscute” is a bad password. “Sj12#8)23&$k51*as.x*3rffalwo@74d*23” is probably a good password. (Please don’t steal that one.)
The problem with creating these super-strong passwords filled with crazy characters and the dreaded “capitalised I or lowercase l” issue is that they’re a pain in the arse to type when you’re trying to use your credentials to log into a third-party service.
For example, if you’re trying to connect your Nintendo Switch to Facebook in order to find friends to play with, you’re going to have to sit there and meticulously type out your uber-secure, 64-character password — and hope you got it all right. It’s even worse if you’re connecting your Smart TV to an online account and you have to manually navigate one of those awful on-screen keyboards with your remote.
Great passwords don’t have to piss you off
The two best password manager apps you can (and should) use are LastPass and 1Password, and they both make it easy to generate randomised passwords for any site or service.
However, there are a few little features you can use to ensure that your password is both strong and fairly type-able, should you ever have to go in and hunt-and-peck it when logging into a service on a device.
You don’t have to create crazy-long passwords
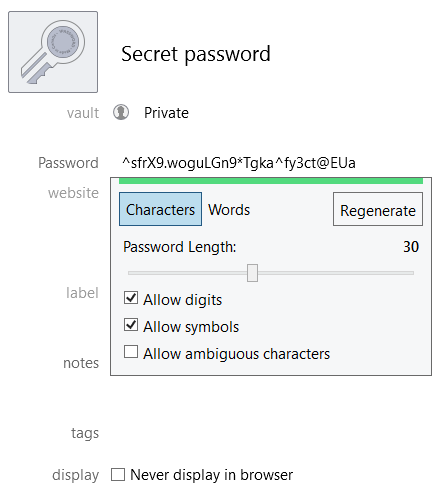
When you’re using either service’s “auto-generation” capabilities, you don’t have to go wild. A 30-character password is going to be a lot stronger than a 16-character password, sure, but beyond the point at which it’s going to matter. As security architect Dameon “PhoneBoy” Welch-Abernathy notes, a 16-character password using just uppercase and lowercase characters — not even wacky symbols — is going to be tough to brute-force.
“The bottom line is, when you actually look at the maths, you don’t need quite as long of a password as you think you do. Assuming the limit is at least 12 characters and all special characters are supported, you can make a complex enough password to sufficiently mitigate most brute force attacks. Even a 16 character password with just mixed case letters has a pretty large search space, assuming your passwords have sufficient entropy.”
Screenshot: David Murphy (1Password)
Avoid symbols or other strange character traps
In both LastPass and 1Password, you have the option to set parameters when auto-generating passwords. Yes, this will make your passwords a little less secure. It will also make them a lot more convenient to type. If your app does a good job randomising characters, they will still be practically impossible to brute-force guess (as noted earlier).
When you’re using 1Password to generate a new password, make sure you’ve unchecked “Allow symbols.” It should be fine to keep using digits, since numbers aren’t nearly as tricky to get to as weird characters that probably require you to switch between different keyboard screens when you’re manually typing them into a device.
While you’re here, also make sure that your “Allow ambiguous characters” is unchecked, because it’s annoying to accidentally type an “I” when you meant an “l,” or a “O” when you meant a “0,’ et cetera.
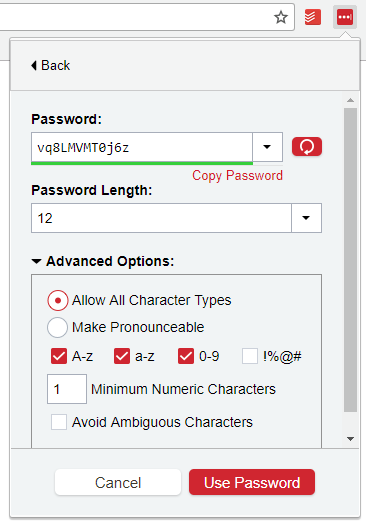
Screenshot: David Murphy (LastPass)
LastPass gives you a little extra customisation. You can set your auto-generated password’s length (of course), but you can also specify whether the password should use the following characters: A-z (sure), a-z (sure), 0-9 (sure), or wacky symbols (pass). You can set a required minimum number of numerals to keep your passwords extra-diverse, and you can also elect to avoid ambiguous characters, which we recommend doing.
What about passphrases?
Theoretically, it’s a lot easier for you to remember a lyrical line from one of your favourite songs — an 84-character password, let’s say — than 84 characters of gibberish. A strong passphrase should be incredibly difficult to brute force, and is a much better solution than simply trying to “mask” a short password in some silly way: “P@$$w0rd123,” instead of “Password123,” for example.
There are only two problems with using a huge passphrase: First, your device (or service) might have some stupid limitation that prevents you from entering a huge password. Perhaps you’re just limited to a maximum character count of 16 digits — still great if you use all 16, but not nearly as great as if you were typing in a 32+ character quote that you love.
Second, you’re still going to have to do a lot of on-screen typing if you’re using your favourite Shakespearean quote as a password. Pulling a passphrase out of a password-management app is easy; having to manually type “itwasthebestoftimesitwastheblurstoftimesitwastheageofwisdom…” a few times on your PlayStation 4 because you made a spelling mistake somewhere in the middle isn’t going to be very fun.
That said, you’ll probably make fewer errors with a common, long phrase than a shorter string of gibberish, so a strong passphrase is definitely worth considering.
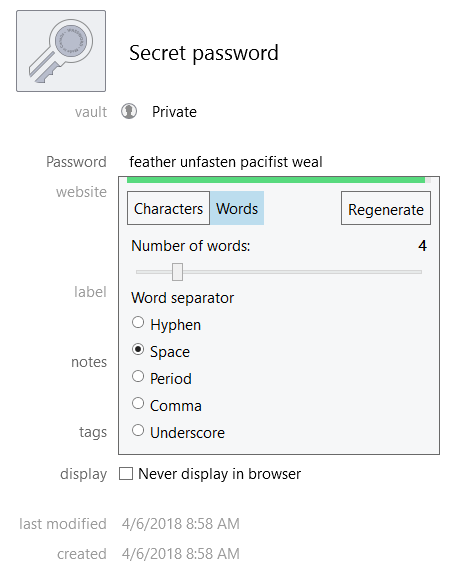
Screenshot: David Murphy (1Password)
If you don’t have any fun phrases in mind, 1Password can help you create passphrases from random words. When auto-generating a password, select the option for “words” instead of characters, and assign your favourite separator to split the words up, such as a period or a hyphen. LastPass has an option for creating “pronounceable” passwords, but that won’t turn your gibberish into words. You’ll have to think of your own clever phrase.

Comments
2 responses to “How To Create Secure Passwords That Aren’t Impossible To Type”
I combine the two. A passphrase on its own might be crackable if someone uses the works of Shakespeare or a lyrics database as a lookup source. But if you add a few easily typed punctuation characters before and after, not so much.
e.g.
Instead of using to be or not to be as your passphrase use ###to be or not to be###. Still easy to remember and type, and better than “2 be or not 2 be” which is also not fooling a brute force attack.
The variation I use for my own passwords (well, the master password for my password manager) is more complex than that but as easy to remember, but if there are any password boffins who can see a flaw with my method I’d love to hear an explanation.
I use an abbreviated passphrase. Combined with factors from the website.
For example,
Phase could be “The wheels on the bus go round and round”
That could then be converted into be “twotbgrar”.
Add some numbers or if your sentence ends with an exclamation/question mark, use that.
Then, if you want a unique(ish) password for each website, use something pertaining to that website in the password. For example, LifeHacker could be LI, or LH, with either the start of each word, or the syllables, or the first few letters.
So, your password could result in “Twotbgrar!64Lif”. Facebook could be “Twotbgrar!64FAC”. As long as you decide on how it’s structured, and you can remember that, you’ll never forget a unique websites password again.