passwords
-
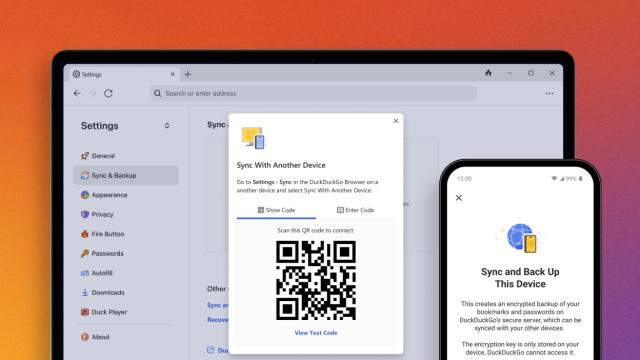
Privacy Browser DuckDuckGo Can Finally Sync Your Passwords
You can finally share your saved passwords between multiple devices without using a workaround or a less-secure browser.
-

How to Switch to Using Passkeys With Your Google Accounts
The future is passkeys, not passwords.
-
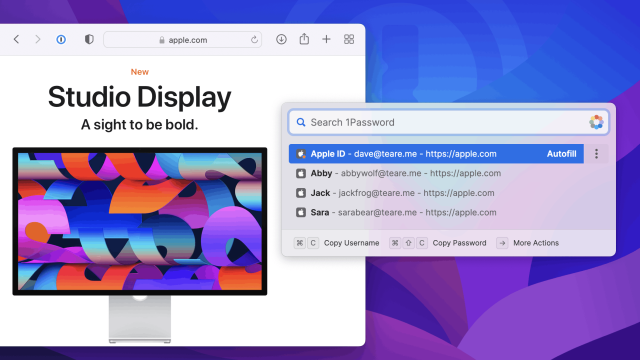
Why 1Password Is Now the Best Password Manager for Mac
For Mac enthusiasts and power users, 1Password has been the password manager of choice for more than a decade. But with a redesign and a new killer feature, we think 1Password 8 is now the best password manager for everyone using a Mac, period.
-

Should I Keep Using My Password Manager?
You should be using a password manager, because it’s one of the best things you can do to secure your digital life. With it, you’ll be able to create strong, incredibly difficult to guess passwords that you won’t even be able to remember yourself. Your password manager will store them for you, and you’ll be…





