cybersecurity
-

How to Switch Health Insurers if You’re Worried About Cybersecurity, Costs or Claims
More than half of Australians hold private health insurance. About one quarter, or almost four million people, are members of Medibank, Australia’s largest health insurer and the company at the centre of the current cybersecurity breach. Medibank has promised to support affected customers. However, such breaches may trigger some customers to think about switching companies.…
-
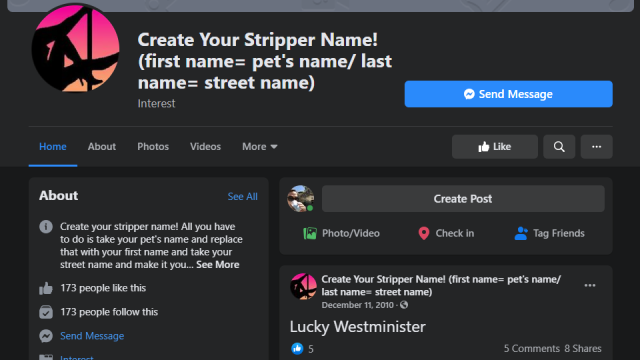
That Social Media Meme Might Pose a Security Risk
This should be common sense at this point, but the fact that they continue to trend on social media suggests plenty of people need the reminder: Stop participating in those weird memes that ask you to provide seemingly innocuous personal information (your full name + the street your grew up on + your first car,…
-
Find The Perfect Excuse For Every Embarrassing Corporate Data Leak
Sometimes I wonder why everyone isn’t getting hacked all the time. We’re all so bad at security, and there are so many people who know how to abuse it! And then I remember that we are getting hacked all the time. Companies regularly dangle all our home addresses and passwords and phone numbers and credit…
-
I’m Cybersecurity Consultant MacKenzie Brown, And This Is How I Work
Hopefully, the first cyber-attack that MacKenzie Brown helps you survive will be a fake one. Otherwise you’ll end up calling her and her colleagues at Optiv Security when you’ve already been compromised by a hack. As an incident response consultant, Brown helps clients prepare for, or recover from, intrusions from hackers. And as the founder…



