In the never-ending battle against security threats on the internet, there’s a new enemy spreading rapidly: Malvertising, or malware downloaded to your computer when you view an ad, even if you use an ad blocker. Here’s what you should look out for, why it’s a problem, and how to protect yourself.
How Malvertising Works
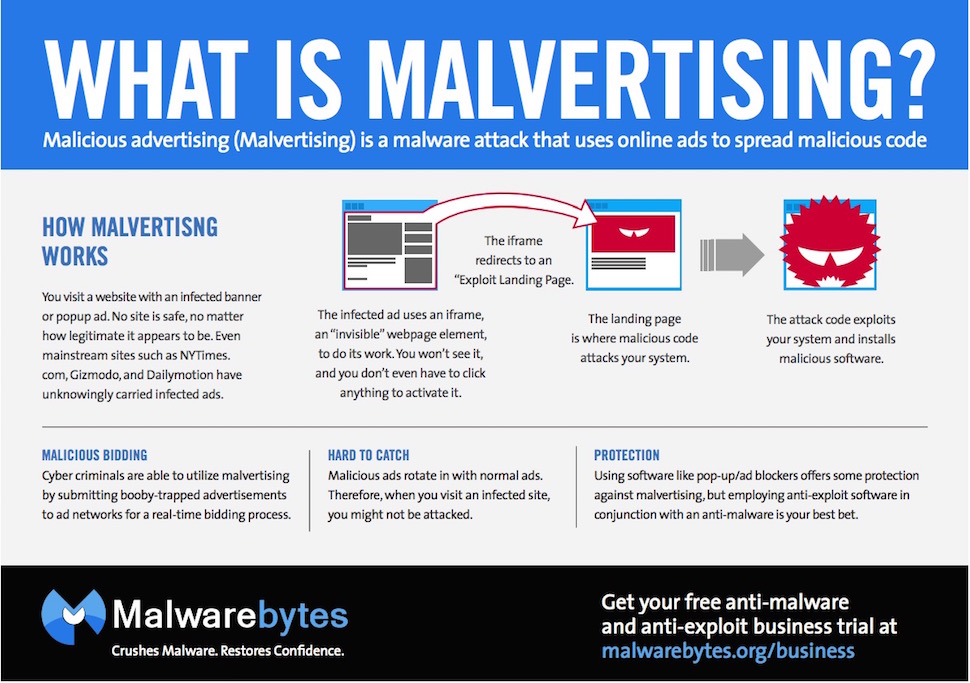
Malvertising is insidious, and can be delivered on a wide scale simply by displaying an advertisements on a web page. It’s usually spread without the knowledge of the site hosting the ads, and without the knowledge of the ad network the malware is riding on. That means that an email to the blog owner that “your ads infected my computer with a virus” will be inevitably met with confusion. Emails from site owners to their advertising partners will get a similar response. And it’s becoming much more common.
If you’ve been around the web long enough, you might remember the days when skeezy ad networks used banner ads and pop-ups to encourage you to download malware, install a toolbar, or change your start page. We told people to “just avoid sketchy web sites and you’ll be fine”. Those days have long since passed. Malvertising is different – it’s injected into well-meaning ad networks, through weaknesses in their security and exploits in their technology. The end result is an ad that doesn’t just prompt you to download something, but one that automatically pushes malware to your system, even if the ad is blocked by an ad-blocker or loads in the background.
Even worse, malvertising can be designed to target specific systems. Because ad networks capture data like your browser, your operating system, and even where you’re physically located (all used to decide which ads to display), an intruder can use the ad network’s own data to present malware specifically built, for example, for Windows XP machines in Australia. It’s a simple matter to attack government agencies by directing infected ads at government employees who still use Windows XP. Alternatively, the malware can only appear to users with Flash enabled, or to Internet Explorer users — anything to improve chances of an infection.
There is good news, though. Ad networks, to their credit, have been tightening up the process for submitting ads so malicious ones don’t slip through the cracks. Plus, knowing that their business rests on the trust that they will serve useful ads to their audience, they act quickly if there’s a compromise. Similarly, on our end of things, much of the malware injected into ad networks makes use of technologies that we all know are vulnerable, like Adobe Flash, Acrobat, and Java.
Disabling Plugins and Using an Ad Blocker are Good Steps (but Not a Cure-All)
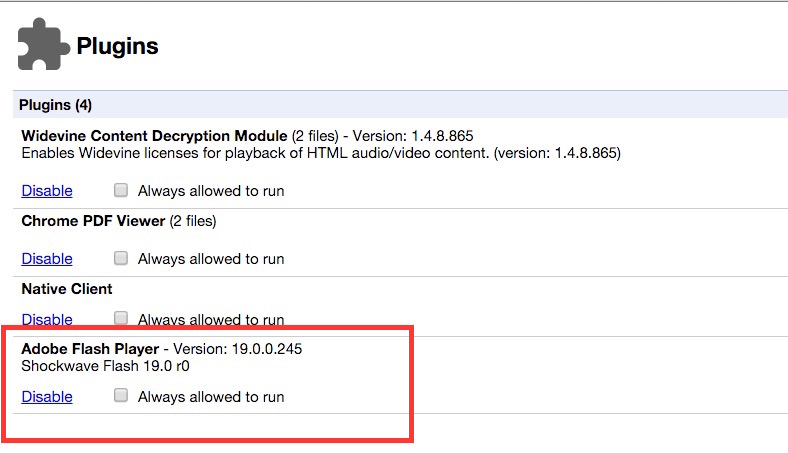
So the solution is just to disable Flash and uninstall Java, right? Odds are you probably don’t need them anymore, so browsing the web without them should make everything better.
That’s a good start, but there’s more to the story. Disabling Flash and Java plug-ins are great first steps, and that will get you a good way to safety, but you should also disable any plug-ins you don’t use, uninstall add-ons you don’t need, and keep your browser updated regularly, as this guide from How-To Geek explains. You might think “oh, it’s just Flash,” but the next vulnerability may not be something so easily disabled — or it could be built-in to your browser.
A lot of malware injected into ad networks is delivered to end computers through Flash and Java, but not all of it. In many cases, they make use of other zero-day exploits, either in the site running the ad (which then prompts you to download malware), or on the computer viewing it (which bypasses the prompt and just infects your computer). For example, when celebrity chef Jamie Oliver’s site was hacked, visitors didn’t get prompts, or alerts — they just got a steaming dose of malware delivered to their computers behind the scenes, thanks to some compromised JavaScript.
So the next step must be to install an ad blocker, right? Never seeing ads must mean you’re protected from malvertising, right?
Not so fast. While ad-blockers and similar tools can certainly help, there are two issues with them right now:
- Ad blockers that prioritise some ads but not others are just as vulnerable. In short, when you install Adblock Plus and think you’re supporting those so-called “non-intrusive” ads, you may be shooting yourself in the foot. In fact, ad networks generally perceived as trustworthy are the biggest targets of malvertising. Yahoo’s ad network was hacked, and subsequently delivered malware to PlentyOfFish users earlier this year. Google’s own DoubleClick network exposed millions to malware, even though the malware involved specifically targeted Windows XP users. To be fair, there’s no evidence that any of this got through ad blockers specifically, but when ad blockers start accepting money from ad networks to be whitelisted, this is the inevitable result.
- Display ads aren’t the only ones being targeted. Most ad blockers can handle display ads just fine, but malvertising is making the leap to video ads now as well. Video ads are harder to vet for quality before being included in an ad network’s database, and they can be disguised as normal commercials, pre-roll ads, or even whole-page takeover ads that a user has to dismiss in order to go back to reading an article, or watching a video.
So the solution here is not just “install an ad blocker,” but “install an ad blocker you know how to use, and use it appropriately.” That means get in there and disable unnecessary scripts and see who’s whitelisted and who isn’t. We recommend uBlock Origin here, and Disconnect offers blocks malvertising on your desktop and on mobile devices as well.
Don’t overlook the importance of to really tackle Malvertising. Combine anti-malware with browser-based tools, and you should be well protected.
If you just install Adblock Plus, load up the default lists, and walk away, you’re doing yourself a disservice. As with any security tool, if you don’t take the time to be an educated user, you leave yourself vulnerable. Not just to the malware or exploits floating around the web, but to the weaknesses in the tools you trust to protect you.
Support a Non-Ad-Powered Web
All of these tools are great, and will let you browse the web in peace and relative security, but they do come at a cost: the sites that are running the ads in question. Punishing every site you visit because a far-off ad network is compromised, especially when it’s not the site owner’s fault, isn’t a very nice thing to do. Of course, we at Lifehacker rely on ads to pay the bills too, but malvertising puts users — and site owners — in a really terrible position.
The rise of massive ad networks that let site owners focus on running their blogs instead of dealing with advertising also makes it near impossible to support the site owner without putting yourself at risk — or putting your data in the hands of those massive networks. You could just whitelist the sites you trust and respect, and let your anti-malware tools do their job if something goes wrong, but there’s another option: When services let you support them directly to avoid ads, do it.
Malvertising is going to continue to be a problem, and while massive ad networks like DoubleClick and TradeDoubler and Yahoo’s own network are all trying to address it, it’s still up to each of us to protect ourselves, lock down our sites, and build the kind of web we want to live on.
Comments