authentication
-
Why You Should Switch From Google Authenticator to iCloud Keychain
Google Authenticator is an excellent solution for generating one-time passcodes for two-factor authentication. But while the app makes a lot of sense to use for many, if you’re locked into the Apple ecosystem, you’re better off using iCloud Keychain. And that’s true now more than ever, as Apple recently made it easy to transfer your…
-
How to Finally Use Google Authenticator Without Your Phone
Ever since it came out, Google Authenticator has been a popular choice for generating two-factor authentication codes on the fly. The service is reliable and secure, but has always had one glaring issue: the inability to sync authentication codes between devices, leaving you at risk of losing access to all of your 2FA accounts.
-

You Shouldn’t Use Your Phone Number for Two-Factor Authentication, Anyway
You should be using two-factor authentication (2FA) with each and every one of your accounts that allows it. You probably already do for at least some accounts, and it probably pisses you off from time to time. Every time you try to log in, you need to find your phone, check the code they texted…
-
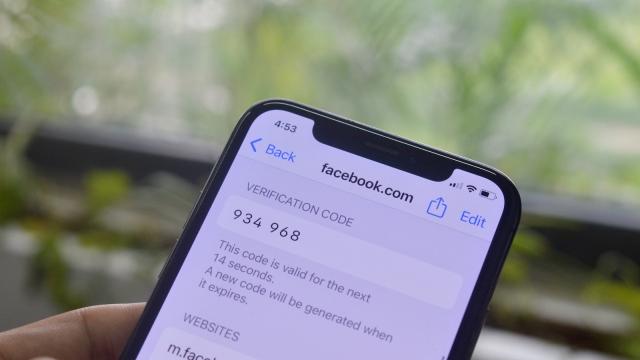
You Should Use Your iPhone’s New Built-in Two-Factor Authentication
When it comes to protecting your accounts, the general consensus is to always use two-factor authentication, which traditionally uses a unique six-digit code that’s re-generated every 30 seconds. If you want to keep hackers away, it’s a big help…but the process isn’t seamless. You often need a third-party app, and you end up losing access…