two factor authentication
-

Turn Microsoft’s Authenticator Into a Password Manager
Microsoft is testing out a new password-management feature in its Authenticator app, which makes the former even more useful as a one-stop shop for all of your account-related information. It’s super easy to set up, and it enables you to synchronise your passwords across iOS and Android, as well as Chrome and Edge on your…
-
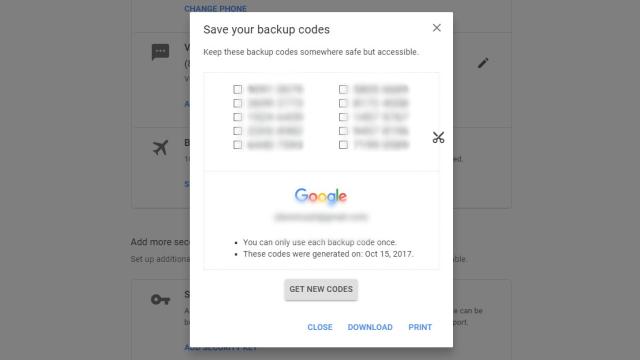
How Do I Get Into My Email If I’ve Lost My Recovery Codes?
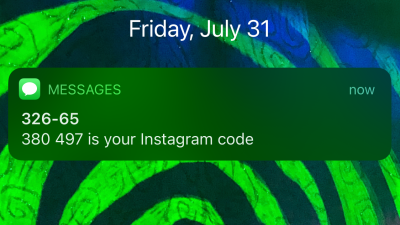
Whenever you get the chance, you should use two-factor authentication to secure your various accounts. That’s a no-brainer. However, I also appreciate services that try to enhance your account security on your behalf ” like, for example, requiring you to input a special one-time code to even reset your password (thwarting anyone who has managed…
-
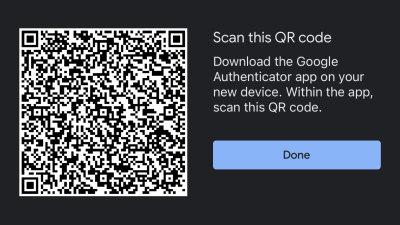
How To Transfer Google Authenticator To Another Android
Google Authenticator is getting its first big update since September of 2017, and you’ll enjoy more than just a few cosmetic upgrades once the updated app rolls out to your Android (and eventually, we hope, your iPhone/iPad).
-
The Best Ways To Stop Hacking Attacks, According To Google
Everywhere you turn, someone is handing out advice about account security and privacy. And while it never hurts to be reminded about all the ways you can protect your critical data, have you stopped to wonder whether any of the various security measures you’re taking are actually effective?