software
-

ChatGPT Plus Has Two Huge New Features You Can Try Right Now
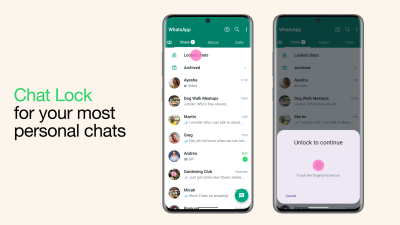
OpenAI’s ChatGPT kicked off what feels like an AI revolution that isn’t slowing down anytime soon. While other big tech companies, like Google and Microsoft, have entered the AI arena, the conversation is still all about ChatGPT. And that probably won’t change after this week, since OpenAI just rolled out two huge features for ChatGPT…
-
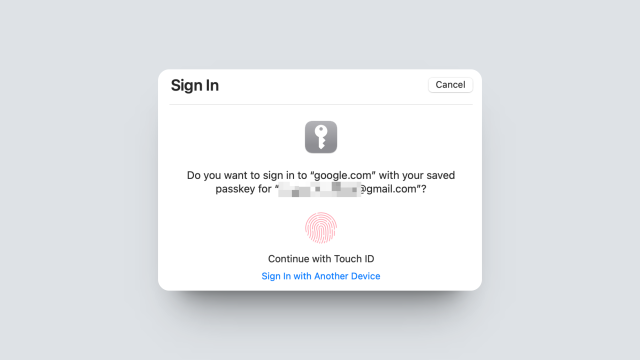
How to Use Passkeys on Your iPhone or Mac
A seamless login future is coming for all Apple users. Starting with iOS 16 and macOS Ventura, Apple offers built-in support for passkeys. You can add these new cryptographically generated keys directly to your iCloud Keychain and they’ll sync across all your devices using end-to-end encryption. As long as a service, app, or website supports…
-
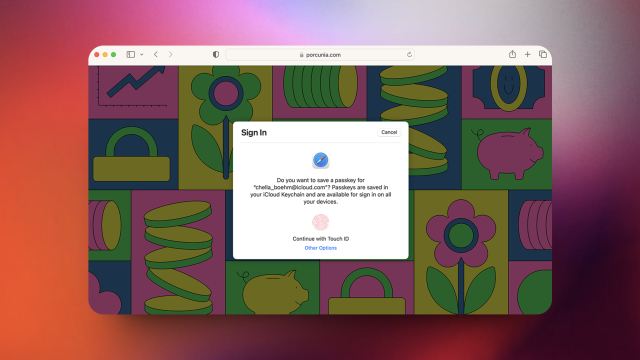
Embrace the Passwordless Future of Passkeys
Digital passwords have existed since the 1960s, and we haven’t come up with a better option…until now. An tech industry-wide group called the FIDO Alliance aims to get rid of them, and for good reason: Passwords are easy to hack, and difficult to remember. The smarter method, they argue, is to scrap troublesome passwords altogether…
-

You Can’t Trust Your Browser’s ‘Lock’ to Tell You a Website Is Safe
When you browse the internet, you probably notice a small lock icon that appears in the URL bar. It’s common internet security advice to look for this lock whenever visiting a new site, to make sure your connection is actually secure. Google, however, announced it will retire the lock, since it doesn’t think it serves…