Security researcher Pawel Wylecial publicly disclosed yesterday a Safari vulnerability that could convince users to secretly send any file on their system to a recipient.
Though Wylecial himself says the bug “is not very serious,” in that it still requires a person to manually do something in order to mistakenly send a file from one’s system to another person — including entering a recipient — “it is quite easy to make the shared file invisible to the user. The closest comparison that comes to mind is clickjacking as we try to convince the unsuspecting user to perform some action.”
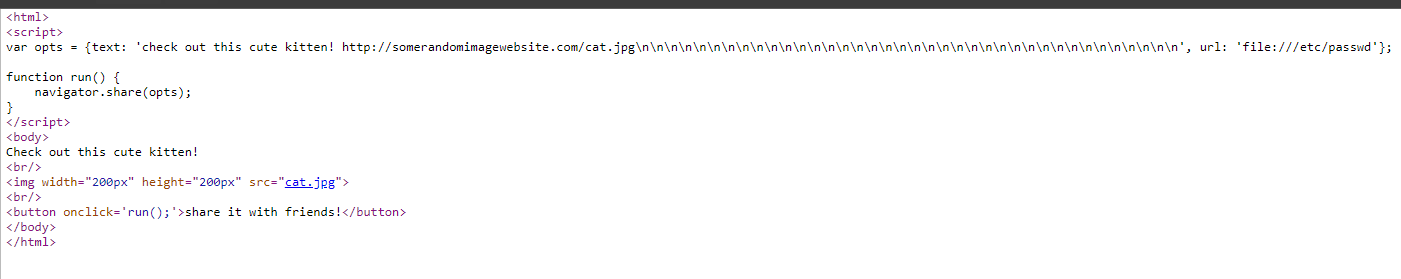
How it works is pretty simple. Safari’s Web Share API supports the file:// URI scheme. As a result, you can incorporate a link to a file on a user’s computer within the same site button a user would otherwise use to share the content they’re looking at via a third-party app.
So, for example, clicking on this button:

and sharing that image via, say, the macOS Mail app, would create a rather innocent message — “check out this cute kitten!” — that would also include your Mac’s “passwd” file, as the button also includes the variable “file:///etc/passwd” in the site’s source code:
If you were paying attention you’d notice the attachment in your email message and probably question and/or quickly delete, but if you weren’t, well, you would have just sent over a file you didn’t mean to send to a recipient. And I can totally see a website abusing this feature by encouraging users to share content to some kind of catch-all inbox for this information.
Again, you’re probably not likely to be duped if you’re decently tech-savvy, but those who are not could get suckered in, especially since it’s hard to tell what file you’re actually sharing when you use other apps to create the message. As Wylecial writes, the Gmail app, for example, mucks up the file name so much that you wouldn’t even know you were sharing your password file (to continue this example).
Wylecial disclosed this vulnerability to Apple in April of 2020. Apple finally replied in July that they’re investigating the issue, and clarified in August that they’ll be patching this in a security update scheduled for the autumn of 2021.

Leave a Reply
You must be logged in to post a comment.