Forwarding ports on your router so devices can talk to the outside world is a pain in the butt, so it makes sense why a technology like UPnP sounds so convenient. This automatic process assumes that it’s safe to expose your network to the internet when internal programs request access ” which is generally true, unless it’s a piece of malware doing the asking.
See the problem? Generally speaking, attackers find creative ways to take advantage of overly trusting UPnP protocols to perform all kinds of fun actions ” up to and including port-scanning your network for additional attack vectors.
There’s no real reason you should be running UPnP. The convenience isn’t worth the risk to your network security. If an app doesn’t work, like your favourite BitTorrent downloading tool, forwarding parts isn’t that difficult of a process. Annoying, sure, but much more secure than relying on UPnP.
If you need more convincing, Ars Technica has a healthy write-up of a brand-new proof-of-concept attack that takes advantage of yet another vulnerability in UPnP to create a gigantic distributed denial of service (DDoS) network out of susceptible devices. Fun!
As Dan Goodin writes:
“The exploit works by abusing the UPnP SUBSCRIBE capability, which devices use to receive notifications from other devices when certain events ” such as the playing of a video or music track ” happen. Specifically, CallStranger sends subscription requests that forge the URL that’s to receive the resulting “callback.”
To perform DDoSes, CallStranger sends a flurry of subscription requests that spoof the address of a third-party site on the Internet. When the attack is performed in unison with other devices, the lengthy callbacks bombard the site with a torrent of junk traffic. In other cases the URL receiving the callback points to a device inside the internal network. The responses can create a condition similar to a server-side request forgery, which allows attackers to hack internal devices that are behind network firewalls.”
So, disable UPnP already
The easiest way to ensure your network doesn’t participate in this kid of botnet is to disable UPnP on your router. It’s easy to do, but the option ” if present ” is likely buried under an advanced settings menu. For example, on a typical TP-Link Archer A20, you’ll find it at: Advanced > NAT Forwarding > UPnP. This makes sense if you’ve messed around with router configurations before, but probably isn’t the first place a regular user will look.
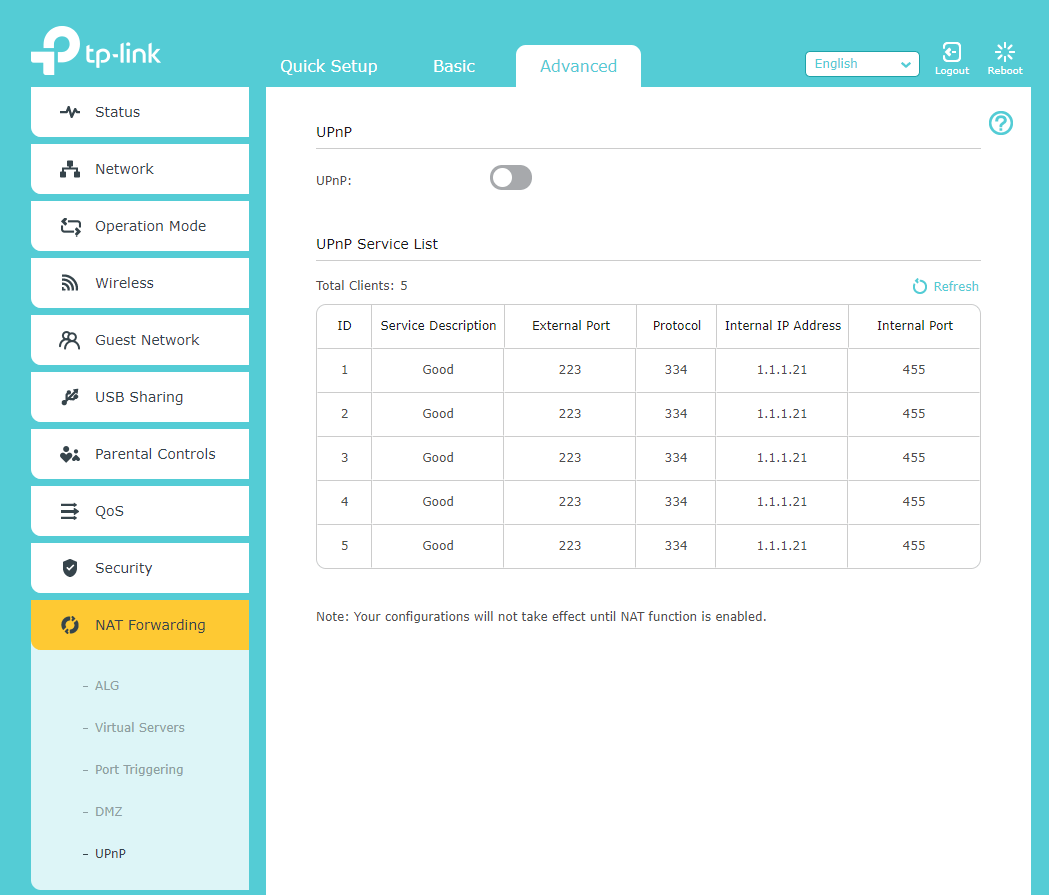
Even on a more user-friendly router like a Google Nest Wifi, you have to dig a bit to find the UPnP settings (again, via the Nest Wifi’s advanced settings):
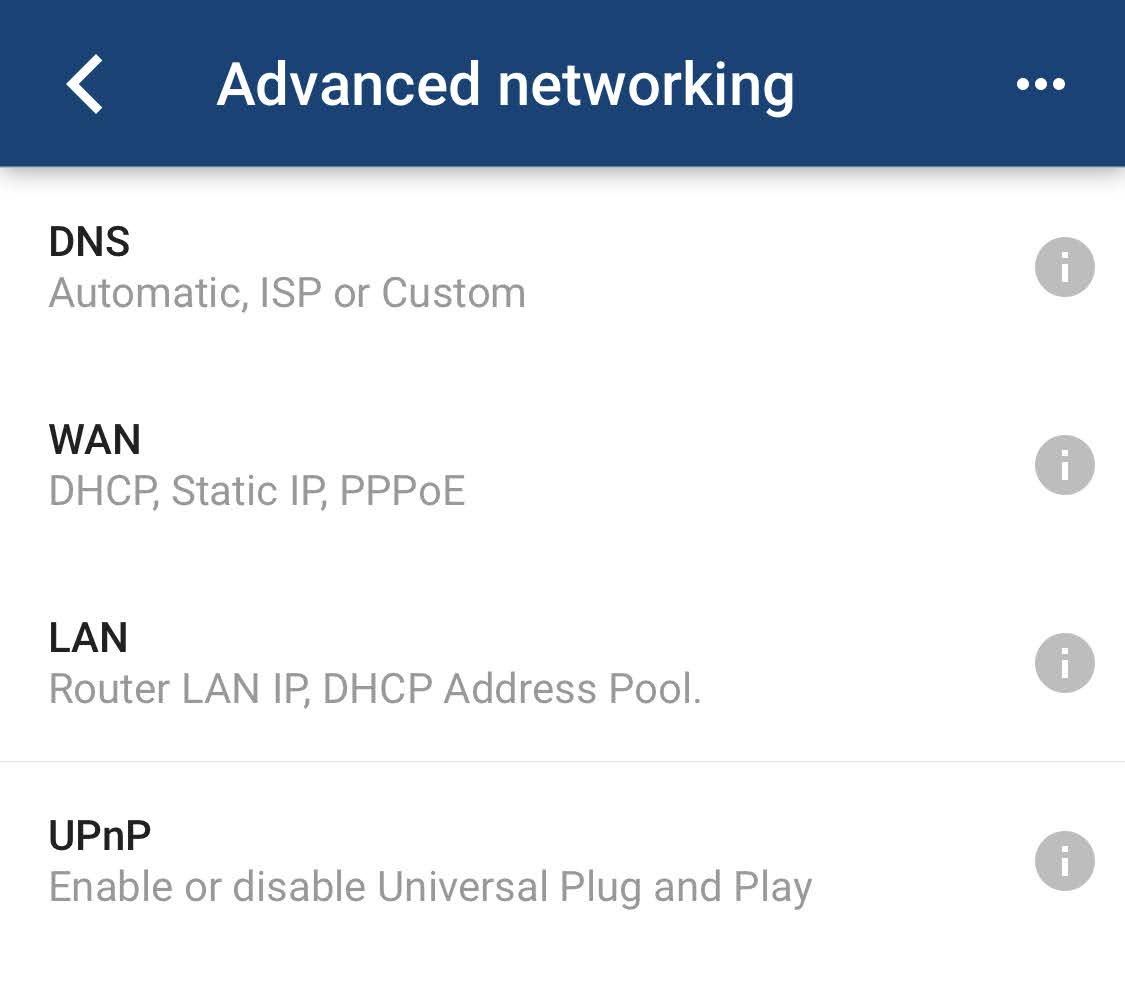
On the plus side, you’ll also now know where to forward ports on your router if any hardware or software in your network requires it to function. Typically your router’s UPnP settings are located in the vicinity of its port-forwarding settings, and all you need to set up port forwarding is the IP address of the device you’re forwarding to, as well as the range of ports required. (It’s easy to figure out!)
Once you’ve made your adjustments, if any, it’s worth using a few online tools to check the security of your network. I recommend trying the “Instant UPnP Exposure Test“ over at ShieldsUp!!, as well as F-Secure’s Router Checker, to see whether your network is opening more ports to the world than it should.

Comments