Shellshock, the newly-discovered vulnerability that allows attackers to inject code into your computer, puts your Mac or Linux machine at a serious risk for malicious attacks. Here’s how to test if your machine is vulnerable.
Shellshock uses a bash script to access your computer. From there, attackers can launch programs, enable features, and access files. The script only affects Unix-based systems, so Linux and Mac are vulnerable while Windows isn’t.
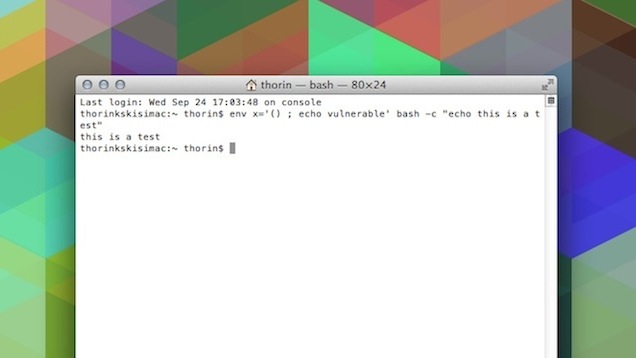
You can test your system by running this test command from Terminal:
env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
If you’re not vulnerable, you’ll get this result:
bash: warning: x: ignoring function definition attempt bash: error importing function definition for 'x' this is a test
If you are vulnerable, you’ll get:
this is a test
You can also check the version of bash you’re running by entering:
bash --version
If you get version 3.2.51(1)-release as a result, you’ll need to update. Head over to WonderHowTo for the guide to update on Mac, and LinuxNewsPro to get the update for Linux.
Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here’s How to Patch OS X [WonderHowTo]
How to patch bash for shellshock in CentOS, Ubuntu, etc [LinuxNewsPro]
Comments
7 responses to “How To Check If Your Mac Or Linux Machine Is Vulnerable To Shellshock”
You fail to mention… That the “attacker” needs to have access prior to executing that command… It comes across as if they execute it they have access to *. Where * is anything.
Unless you’re running a website in bash or your web server’s “referrer” is linked to a bash script (for whatever reason..) they need access prior to running the command..
Also the whole post looks rushed..
If we can get people to microwave their iPhone 6s and get them to bend their 6 Plus, we can get people to run commands in terminal
Perhaps call them up and tell them that Macs don’t have viruses because Apple techs are working hard 24/7, and to ensure it stays virus-free, you need to run a virus-free command on your Mac because it couldn’t be contacted by Apple.
You test code is missing some syntax. It should be: env x='() { :;}; echo vulnerable’ bash -c “echo this is a test”
For anyone that might find these technical details too hard to digest, i’ve created a .pkg installer to patch bash and sh as per lifehacker’s post.
https://www.dropbox.com/s/0gwor9etpjy4kwk/Shellshock-CVE-2014-6271-Patch-20140926.pkg.zip?dl=0
Also on JAMF Nation: https://jamfnation.jamfsoftware.com/discussion.html?id=11914 if you want some more details.
Comes with absolutely no warranty! But i’ve tested on 10.10 beta, 10.9 and 10.8 and all are no longer vulnerable after running the installer.
Apple will likely release an update in the coming weeks but they’re notoriously slow at doing so!
Cheers!
The irony in this post is that you are actually giving people commands to run in their command line, to see if they are vulnerable to an attack based on entering code into the command line… and then people are making package installers that supposedly automate this process…hiding the commands further…
I was just thinking that.
Also 3.2.5 is pretty old.
Heh well .. Any patches to bash are just quick and dirty fixes it is still vulnerable by running the below. (if you don’t have sh linked to bash, use bash instead of sh in the below)
What the above does is creates a file called echo with the current date output, then executes cat echo.
You’ll end up seeing something like this, take notice to the date at the end.
Thanks to – https://twitter.com/taviso/status/514887394294652929 for the tip.