Dear Lifehacker, I’ve been hearing a lot about Tor these days, but I’m not entirely sure what it does or why I’d ever use it. What exactly does Tor do? Sincerely, Frank Overwood
Dear FO,
We’ve talked a lot about Tor over the years, because it’s the easiest way to browse the web anonymously. But it’s not always clear why that matters or why you’d need to use it. Let’s take a look at what Tor does, who uses it, and what Tor doesn’t do.
What Tor Does
Tor is short for The Onion Router (thus the logo) and was initially a worldwide network of servers developed with the US Navy that enabled people to browse the internet anonymously. Now, it’s a non-profit organisation whose main purpose is the research and development of online privacy tools.
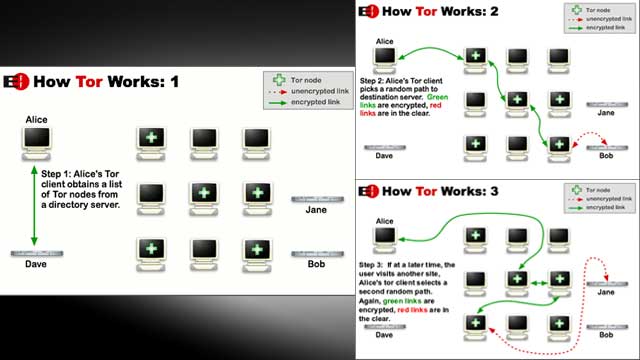
The Tor network disguises your identity by moving your traffic across different Tor servers, and encrypting that traffic so it isn’t traced back to you. Anyone who tries would see traffic coming from random nodes on the Tor network, rather than your computer. (For a more in-depth explanation, check out this post from our sister blog, Gizmodo).
To access this network, you just need to download the Tor browser. Everything you do in the browser goes through the Tor network and doesn’t need any setup or configuration from you. That said, since your data goes through a lot of relays, it’s slow, so you’ll experience a much more sluggish internet than usual when you’re using Tor.
What Tor Is Good For
If you want to be anonymous — say, if you live under a dictatorship, you’re a journalist in an oppressive country, or a hacker looking to stay hidden from the government — Tor is one of the easiest ways to anonymise your traffic, and it’s free. It’s far from perfect, though (we’ll get to that in a moment).
On a more general level, Tor is useful for anyone who wants to keep their internet activities out of the hands of advertisers, ISPs and websites. That includes people getting around censorship restrictions in their country, police officers looking to hide their IP address, or anyone else who doesn’t want their browsing habits linked to them.
Tor’s technology isn’t just about browsing anonymously. It can also host web sites through its hidden services that are only accessible by other Tor users. It’s on one of these hidden service sites that something like The Silk Road exists to traffic drugs. Tor’s hosting capabilities tend to pop up in police reports for things like child pornography and arms trading too.
So is it something that everyday users need? Probably not, at least not yet. But it’s become popular because of its usefulness in many of these more specific situations.
What Tor Doesn’t Do

Tor is handy, but it’s far from perfect. Don’t think just because you’re using Tor that you’re perfectly anonymous. Someone like the NSA can tell if you’re a Tor user and that makes them more likely to target you. With a enough work, the government can figure out who you are. Vice points to a recent FBI bust that shows how this might work:
The FBI’s big child porn bust this summer also raised some suspicion from privacy advocates over how easy it is for the Feds to infiltrate Tor. The FBI managed to crack the anonymous network by injecting malware into the browser, in order to identify what it called “the “largest child porn facilitator on the planet.” In the process, the malware revealed the IP addresses of hundreds of users.
Furthermore, anonymity is not the same as security. It’s hard to hack into the Tor network, but the browser is a different story. As we found at least year, the NSA can get into your browser a lot easier than it can the network and once it does, it gets access to everything else. So, “man in the middle” style attacks on Tor are still possible with help of internet service providers. Tor responded to these possible attacks with these comments:
The good news is that they went for a browser exploit, meaning there’s no indication they can break the Tor protocol or do traffic analysis on the Tor network. Infecting the laptop, phone, or desktop is still the easiest way to learn about the human behind the keyboard.
Tor still helps here: you can target individuals with browser exploits, but if you attack too many users, somebody’s going to notice. So even if the NSA aims to surveil everyone, everywhere, they have to be a lot more selective about which Tor users they spy on.
Just using Tor isn’t enough to keep you safe in all cases. Browser exploits, large-scale surveillance, and general user security are all challenging topics for the average internet user. These attacks make it clear that we, the broader internet community, need to keep working on better security for browsers and other internet-facing applications.
As the How-To Geek points out, you still need to use HTTPS whenever possible to protect yourself from man-in-the-middle style attacks. Likewise, Tor’s only as strong as its browser, which has had security flaws before, so it’s worth making sure you always have the newest version.
So Should You Use Tor?
As we mentioned above, if you’re an average user looking at cat GIFs and browsing Facebook, you probably don’t need to worry about the government spying on your activity, and Tor is just going to slow down your connection. It’s more likely that you need to secure your internet rather than anonymise it, say, when you’re using public Wi-Fi. In that case, you’d want to make sure you’re using HTTPS on all sites that support it, and possibly even use a VPN to encrypt all your traffic when you’re away from home.
If you want to stay anonymous because you’re downloading large files and don’t want people to see what you’re downloading — say, on BitTorrent — Tor is not a good solution. It won’t keep you anonymous, and you’ll slow down everyone else’s traffic for no reason. In this case, you’d want a proxy or a VPN instead.
In other cases where you want to stay anonymous, Tor will do the trick, and it will do it easily. But we recommend considering a VPN too — as long as you use a VPN dedicated to anonymity that doesn’t keep logs of your traffic, it can provide quite a few advantages over Tor (although you’ll usually have to pay some money).
Most importantly, remember that nothing is 100 per cent anonymous or secure, whether you’re using Tor, a VPN or anything else. If you think you need something along these lines, think about what exactly you’re doing and what you need to protect — half the battle is picking the right tool for the job.
Cheers
Lifehacker
Got your own question you want to put to Lifehacker? Send it using our [contact text=”contact form”].

Comments