We talk a lot about both privacy and security here at Lifehacker, and staying on top of them often feels like a lot of work. So we decided to run through a few of the most popular security and privacy measures, from chat encryption to secure backups, and find the easiest ways to make your online life secure.
Encrypt Your Email
What it Does: Encryption turns your email into a code that can only be deciphered with a key, then sends it to the recipient, who can only read it if they have the same key.
We’ve walked you through setting up email encryption before and it’s easy to do. It takes a few minutes to get set up. I used Mailvelope for Gmail to do it. Mailvelope is just an extension, so it doesn’t take much time to set up.
Set Up Time: 5 minutes.
Annoyances: The biggest problem with email encryption probably isn’t you, it’s the people you send emails to. Both you and the recipient need the encryption software because when you email something to someone, they have to decrypt it on their end using a key you send them. This means you need to first send them the decryption key by another form of communication like phone or text, then they need to go through the trouble of decrypting it on their end using the same software you did.
Nobody is going to want to do this. Pretty much everyone I tried to get to send encrypted messages to just laughed at me. Let’s be honest: most of us aren’t going to encrypt everything we send, because there’s really no point in doing it. After all, sending an email to your parents asking for a news update isn’t really worth encryption. However, sending an email to your parents asking for their bank account details is worth it. But that’s it for most of us.
How Secure Is it?: Like anything, email encryption has vulnerabilities, but it’s a secure way to communicate for the most part. It certainly won’t keep you out of the gaze of the very focused eye of the government, but the 12-year-old hacker down the street probably won’t be able to snoop in on your email. If you need encryption beyond webmail, we recommend the Enigmail Project.
Encrypt Your Chat Conversations
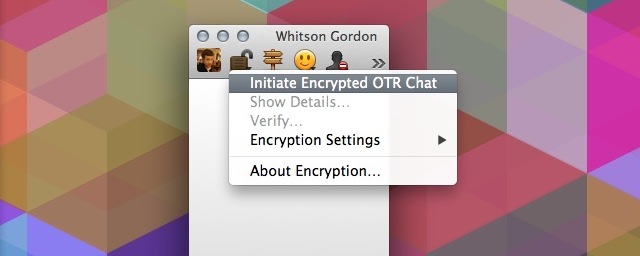
What it Does: Most chat clients use an encryption called Off-the-Record Messaging to encrypt your messages. This makes it so that in order to read an IM conversation the recipient needs authentication by you.
Like email, you might also want to encrypt your instant message chat conversations. Also like email, this is incredibly easy to do. I set up a couple of different methods for this. First off, encryption is easy to turn on in a chat client like Adium by just clicking on the lock icon in a chat (Pidgin users can get this as well). This turns on Off the Record Messaging that’s encrypted, authenticated and not stored. With Adium, your setting is attached to your account (or to a specific contact) so you don’t have to go through and set this up every time. Basically, it’s a “set it and forget” method of encryption.
Setup Time: 30 Seconds.
Annoyances: Chat encryption is actually super simple and doesn’t really have a lot of downsides. The nice thing about how Adium handles it is that it only takes a single step to set up, and then it’s on for good. The person on the receiving end needs either Adium or Pidgin installed as well, but for the most part it’s super easy. The only real downside is that you also want to get rid of chat transcriptions, which can be helpful if you need to revisit conversations.
How Secure Is it?: For most of us, OTR encryption is plenty. It’s tough to crack, and takes a lot of time to do it. OTR is primarily about keeping conversations private and it does a good job with it. I used the Adium settings because I use Adium all day long anyway, but you have other options for keeping conversation private as well. For something even more disposable and encrypted, we’d also recommend software like Tor Chat or Cryptocat for group conversations.
Use Secure Backups and File Syncing

What it Does: Encrypts your data so third parties don’t have access to your files. This ensures that if a backup or file syncing site is hacked, your files can’t be accessed.
Whether you’re using a service like Dropbox for file syncing or a full backup like Crashplan, you don’t want people snooping around in your private data. Likewise, file encryption is just as useful if you have a ton of roommates who you suspect might be snooping in on your computer at home.
Encryption is pretty easy to set up. Crashplan does it automatically for you, so you don’t need to do anything at all. With a service like Dropbox, you actually have a few options. You can encrypt your files manually before you upload them, or use a service like SafeMonk to encrypt them before they’re uploaded. Since I don’t have a lot of sensitive data to worry about, I opted to use TrueCrypt to encrypt anything personally identifiable I had on Dropbox.
Setup Time: 15 minutes
Annoyances: TrueCrypt makes it pretty easy to encrypt everything you need to, but once it’s encrypted you can’t use it from another computer or mobile device. This is fine in most cases. I only encrypted files in Dropbox like medical records and scans of some personal data so it doesn’t matter if I can access it from my phone. Once I started, I realised that the number of files I need to encrypt is pretty minimal.
How Secure Is it?: There’s never such a thing as an uncrackable encryption, but TrueCrypt is reliable for securing your data. Of course, TrueCrypt is secured with a password, so don’t go leaving that around. If you’d prefer, you can also just go entirely off the grid using something like a Raspberry Pi as a Dropbox clone. This way you’re the only one who even knows your file syncing service exists. Another option is to go from Dropbox to another cloud storage service with encryption built in like one of these. Switching from Dropbox over to a service like Spideroak only takes as long as it takes to backup all your data again, so that’s a viable option as well. The benefit is that once you’ve made the switch you don’t have to think about it anymore, but you do miss out on some of the collaborative features Dropbox has to offer.
Hide Your Web Traffic
What it Does: Between privacy-protecting extensions. I opted for the less intrusive browser extensions.
Setup Time: 5 minutes.
Annoyances: The bulk of the privacy extensions don’t cause much trouble and are actually pretty helpful. In reality, it’s something everyone can set up. It takes a few minutes and for the most part you won’t even notice they’re running.
How Secure Is it?: Browser extensions help mask what you’re doing, but they don’t take care of everything. To really privatise what you’re up to, you’ll also need a VPN. It’s hard to justify the work needed to get a VPN set up unless someone wants to intentionally hide something. Sure, you can use a proxy to hide your BitTorrent traffic, or just use a browser like Tor to hide some traffic. If you want to use the internet all the time privately, you’re going to sacrifice some conveniences.
Use a Password Manager
What it Does: A password manager randomly generates all your passwords for web sites and locks them behind a single master password only you know. This means you only have to remember a single password.
Setup Time: 30 minutes to one hour.
Annoyances: We’ve compared a bunch of the different password managers before, but unfortunetely none of them are super user friendly. In fact, they all have their own weaknesses. LastPass is confusing to newcomers and it takes a while to get into using it properly. Likewise, it’s pretty pointless to start using something like LastPass unless you’re actually going to go through and set new passwords for all your accounts, which can take a long time if you use a lot of different services. If you jump around between computers, say from work to home, then you need to install your password manager on all your systems. Otherwise you will lock yourself out of accounts because you can’t remember the password.
Once they’re set up and going, a password manager is fantastic, but it takes a lot to get to that point. In fact, for a password manager like LastPass, we have both a beginner’s guide and an intermediate one along with supplementaltips as well.
How Secure Is it?: Any password manager is only as secure as your password, but they’re still pretty strong. You’ll also need a strong password no matter what.
Use Two-Factor Authentication
What it Does: Two-factor authentication is available on a lot of services these days. Essentially, it’s a simple feature that asks for more than your password. It requires something you know (like your password) and something you have (like your phone). For example, to log into your Google account, you’d need to type in your password, wait for Google to send you a text message with a code, and then type that in before you could access your account on a new machine.
Setup Time: 15 Minutes.
Annoyances: Two-factor authentication is one of those solutions that sounds way more annoying than it actually is in practice. Once you get it set up on all your devices and services, it pretty much disappears into the background. Most services, like Facebook or Twitter, only require a single authentication on each device. So, once you set up and verify your identity once, you’re good to go. Other services, like Google, require you to authenticate every 30 days. Provided you have your phone with you, this only takes a few seconds each time.
How Secure Is it?: Two-factor authentication is incredibly secure because hackers always need at least two of your devices to get into your account. Obviously this is still possible, but it’s less likely that someone will have both your phone and your laptop than just one device.
Like anything with privacy, it’s really about picking and choosing your battles. Certain aspects of privacy and security, like passwords, effect all of us, and everyone could stand to benefit from implementing things like two-factor authentication. Others, like encrypting your data backups, are only important for a small subset of your files, but it’s well worth the few minutes it takes to ensure they’re locked away safely. Really, it’s at a point these days where it’s only mildly inconvenient to keep your data away from prying eyes, and if you’re willing to spend a couple hours setting everything up, the rest happens automatically.
Photos by J Lesselich, biker_becca, geralt, geralt
.

Comments
One response to “How To Make Your Entire Internet Life More Secure In One Day”
It’s really not that hard and is well worth it if you share a network with other people, especially public wi-fi networks. Also gets around geo blocks as you can choose a gateway from many countries. I use Privateinternetaccess and never had a problem but there are many others.
The default client is very quick and easy to setup although i use OpenVPN
I find that it works best to have two separate email systems, one for business and another one for junk and newsletters. So I use Gmail for junk and SaluSafe encrypted email for anything important.